- The most common approach to the protection problem is to make access dependent on the identity of the user.
- The most general scheme to implement identity-dependent access is to associate with each file and directory an access-control
list (ACL) specifying user names and the types of access allowed for each user.
- This approach has the advantage of enabling complex access methodologies. The main problem with access lists is their length. If we want to allow everyone to read a file, we must list all users with read access.
- This technique has two undesirable consequences:
- Constructing such a list may be a tedious and unrewarding task, especially if we do not know in advance the list of users in the system.
- The directory entry, previously of fixed size, now needs to be of variable size, resulting in more complicated space management.
- These problems can be resolved by use of a condensed version of the access list. To condense the length of the access-control list, many systems recognize three classifications of users in connection with each file:
- Owner. The user who created the file is the owner.
- Group. A set of users who are sharing the file and need similar access is a group, or work group.
- Universe. All other users in the system constitute the universe.
- With this more limited protection classification, only three fields are needed to define protection. Often, each field is a collection of bits, and each bit either allows or prevents the access associated with it.
- For example, the UNIX system defines three fields of 3 bits each
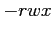 , where
, where 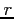 controls read access,
controls read access, 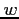 controls write access, and
controls write access, and 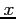 controls execution.
controls execution.
- In this scheme, nine bits per file are needed to record protection information.
Cem Ozdogan
2010-05-05